
Understanding these hidden risks is the first step toward safeguarding your digital life.
1. The Craft of Spear Phishing and Whaling
While general phishing attacks cast a wide net, hoping to catch any unsuspecting user, spear phishing and whaling are far more dangerous because they are highly targeted.
The Hidden Risk: These attacks bypass generic spam filters and prey on trust and urgency, leading to significant financial loss, data breaches, and reputational damage.

2. Business Email Compromise (BEC) Scams
BEC is one of the most financially damaging online crimes. It often involves an attacker impersonating a high-level executive (like the CEO or CFO) and sending an email to an employee responsible for finances. The email typically requests an urgent wire transfer to a fraudulent account or a change in payment details for a vendor.
The Hidden Risk: BEC scams rarely involve malicious links or attachments, making them hard for traditional security tools to detect. They exploit human trust and organizational hierarchies, resulting in massive financial losses that are often unrecoverable.

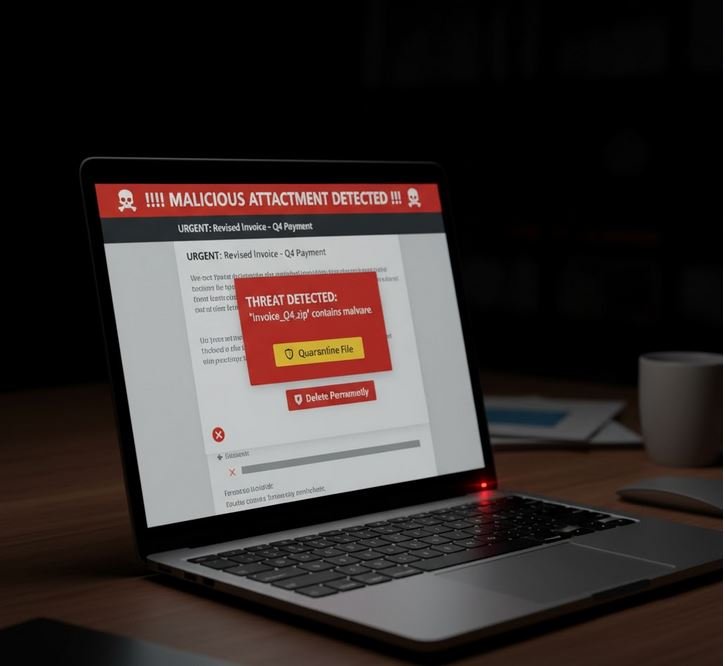
3. Malicious Attachments and Ransomware
While many users are now cautious of executable files, attackers have become more sophisticated. Malicious code can be hidden in seemingly harmless file types:
The Hidden Risk: Opening such an attachment can instantly infect your system with malware, including ransomware that encrypts your files and demands payment, or spyware that steals your personal information without your knowledge.
4. Zero-Day Exploits
A zero-day exploit refers to a vulnerability in software that is unknown to the vendor and therefore has no patch available. Attackers discover and exploit these flaws before the software developers even know they exist.
The Hidden Risk: An email might contain an exploit that targets such a vulnerability in your email client or operating system. Because it's "zero-day," your antivirus and security software might not detect it, making you highly susceptible to immediate compromise.
5. Tracking Pixels and Data Collection
Not all email risks are about immediate infection or fraud. Many emails, including newsletters and marketing communications, contain tiny, invisible images called tracking pixels.
The Hidden Risk: These pixels can reveal when and if you opened an email, your IP address (which can infer your location), and even what device you used. While often used for legitimate marketing analytics, this silent data collection contributes to your digital profile, making you a more valuable target for more sophisticated attacks. It also erodes your privacy without your explicit consent.
Safeguarding Your Inbox: Vigilance is Key
The evolving nature of email threats means that no single solution offers complete protection. A multi-layered approach combining technology and user awareness is crucial:
Email is an indispensable tool, but it's also a gateway for sophisticated cyber threats. By understanding the hidden risks and adopting a vigilant approach, you can significantly reduce your exposure and protect yourself from the dangers lurking within your inbox.
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0