
Quantum computers are not only faster; they are a different kind of technology. Using quantum mechanics, they can solve some problems in seconds, which would take millions of years for classical computers. One alarming example is Shor’s algorithm, which can break most modern cryptographic protocols, including RSA and Elliptic Curve Cryptography (ECC). These algorithms protect everything from online banking to military communications and networks.
Experts predict that large-scale, fault-tolerant quantum computers that can run Shor’s algorithm may appear within 10-15 years (according to the estimates of IBM and Google quantum teams). When that happens, the attackers will be able to decrypt the sensitive data, forge digital identities, and compromise critical infrastructure. The clock is ticking.

Conventional security postures are based on the assumption that everything within the network is secure, which is incorrect in the current environment. Zero-Trust Architecture changes this perspective with the help of a single principle: Never Trust, Always Verify. It means that every user, device, and application is considered a potential threat and requires confirmation of its good intentions.
Here’s why ZTA stands out:
For instance, Google’s BeyondCorp initiative, a real ZTA implementation, migrated security from the network perimeter to device and user verification and successfully adapted to a cloud-first environment. It is not just a reduction of the attack surface; it is the creation of a quantum-ready fortress.

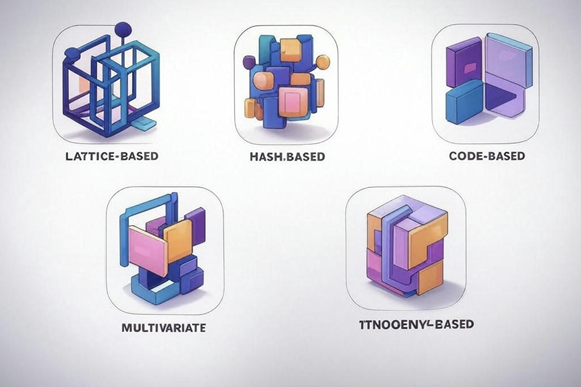
ZTA is powerful, but it is not the only solution. To respond fully to quantum threats, we need quantum-resistant cryptography – the algorithms intended for use against quantum attacks. The National Institute of Standards and Technology (NIST) is the leading body in standardizing options like these:
These, combined with ZT,A provide a layered defense. Picture a cybersecurity onion: peel one layer, and another stands strong.
ZTA and quantum-resistant cryptography are not something that can be implemented easily. The challenges organizations encounter in the process are listed below:
However, the cost of doing nothing is greater than the cost of doing something. A single quantum breach could cripple a company or a country.

Quantum computing is a two-edged sword: a great invention and a cyber threat. With the help of Zero-Trust Architecture and quantum-immune cryptography, organizations can defend themselves. The way is long, but the action should be taken now for the future. Ready to fortify your defenses? The quantum era waits for no one.
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0