
Not all permissions are harmful. Some are necessary to improve the functionality and user friendliness. Thus, it’s important to keep a balance between caution and convenience.
There are several reasons why apps ask for permission. Let’s check below:
App functionality determines the overall value and usability of an app. It refers to how a user can avail its features and capabilities to perform a specific activity or task on his device. Allowing permissions for each app is necessary for it to function properly.
For example, you can send messages through WhatsApp to your contacts only if you allow it to use your contact list. Just like that, you can instantly capture & upload a photo to your Instagram story, only if you permit Instagram to use your camera. It’s how every application on your device functions properly.
If you don’t allow any of those apps, they won’t be functional optimally. Thus affecting the user experience.
This one is interlinked to what we mentioned above. The second reason why permissions are crucial is, they allow applications to perform optimally, which gives a great user experience in return. This kind of seamless interaction not only benefits the user but also supports more effective lead nurturing efforts by keeping users engaged and guiding them naturally through the app, allowing easy navigation, intuitive experience, and avoiding unnecessary pop-ups.
For example, most fitness apps use specific features of your device, including sensors, activity tracking, calendar, the phone's GPS, push notifications for reminders and alerts, to provide you with accurate information regarding your workout schedule or fitness goals. Without these, you won’t be able to track your personal target, wins, or achievements.
Not all requests for permissions are a threat to your security and privacy. Data access needs to be a privilege, and not a right. If an application accesses your device by default, it can compromise data security, especially when downloading suspicious applications.
Various applications only request permission where necessary. For example, a calculator on your device shouldn’t request access to your camera or your contact list, or your photos. If it does, it’s simply overreach: all apps must have appropriate access rights. In such cases, we should say ‘no’.
When you tap allow, you grant permission to access various features like camera, microphone, contacts, etc on your phone. You can also alter permissions on your device anytime you want by going into the ‘app & permission’ section on Android.
Your device will ask you if:
Common types of requests are:
Users can choose based on their specific needs. For example, if you use WhatsApp to make calls more frequently, you probably wouldn’t want to use the option, ‘ask whenever you open the app’; instead, you can give it continuous permission.
Let’s suppose you’ve just downloaded WhatsApp on your device. The moment you try to open it, it will ask for permission to access your contacts, microphone, camera, media, etc.
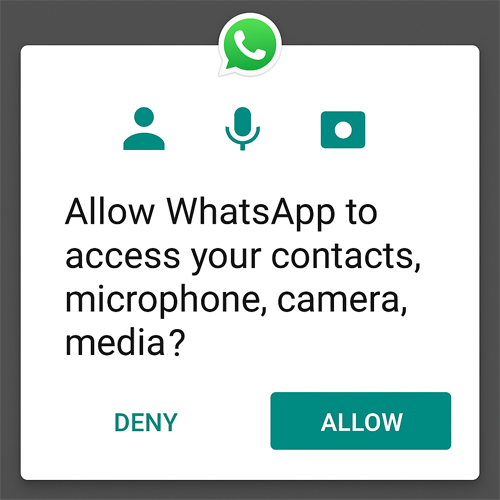
Once you allow it, WhatsApp accesses all your contact details, camera, and microphone, so that you can make calls easily. If you deny access, you will not be able to make a call using WhatsApp.
The term ‘Permission Abuse’ is common for applications that unnecessarily want to access your personal data. For example, a shopping platform might ask for your phone location or gallery before you even start browsing the products. One careless tap on the allow option can invade your privacy and data, and access all your family's info on the phone.
Data theft is a serious challenge users face online, and it can be the result of an app's approachability to your device. For organizations developing or managing mobile apps, it’s critical to test for vulnerabilities before they reach users.
The following risks can arise when careless access is granted:
Always consider the following cases when using an application to identify whether or not it’s a suspicious app:
Understanding and managing permissions and access requests is no longer optional; it’s essential for protecting your personal data. Stay informed, stay cautious, and take control of what your apps can access.
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0