
The moment you decide to sell, donate, or recycle an old computer, smartphone, or tablet, you face a critical security risk: the data stored on it. Simply hitting "delete" or performing a basic factory reset is not enough. Your sensitive information—from banking details and work documents to personal photos—remains recoverable using simple, readily available forensic tools.
This comprehensive guide delves into the essential practice of secure data wiping (also known as data sanitization) to ensure your data is permanently and irreversibly erased before any device leaves your hands. Protecting your digital footprint is not just about privacy; it's about maintaining compliance and safeguarding yourself against identity theft and corporate espionage.
Why Simple Deletion Isn't Secure Data Wiping
Most people mistakenly believe that moving a file to the recycle bin or even formatting a drive makes the data disappear forever. This is a dangerous myth.
When you delete a file, the operating system (OS) simply removes the pointer (the file's address) to that data on the storage device. The actual data remains intact, marked as "available" space for new data to eventually overwrite. Until that happens, the old data can be easily recovered. Similarly, a factory reset on a smartphone often only removes the top layer of user data and settings, leaving deeper data structures vulnerable.
Secure Data Wiping, or Data Sanitization, is the process of destroying or permanently removing the data, rendering it unrecoverable by any known means.
The Gold Standard: Secure Data Erasure Methods
The method you choose for data sanitization depends primarily on the type of storage media (HDD vs. SSD) and the sensitivity of the data. The following are the industry-recognized, secure methods:
1. Data Overwriting (The Most Common Method)
This is the most common and environmentally friendly method, as it allows the device to be reused. Specialized software is used to overwrite the existing data on the storage device with meaningless binary patterns (typically sequences of zeros, ones, or random characters).
|
Standard |
Description |
Media Type |
|
Single-Pass Overwrite |
Writes zeros, ones, or a random pattern over the data once. This is generally sufficient for modern HDDs. |
HDDs |
|
3-Pass Overwrite (DoD 5220.22-M) |
Writes a character, then its complement, and finally a random character, with verification steps. Once a military standard, it's considered overkill for modern drives but still widely trusted. |
HDDs |
|
NIST SP 800-88 "Clear" |
The modern standard, which recommends overwriting all user-addressable storage locations once. |
HDDs |
Note for SSDs (Solid State Drives): SSDs use a technology called wear-leveling, which complicates the overwriting process, as data might be stored in inaccessible "spare cells." For most modern SSDs, the best and fastest method is Cryptographic Erasure or using the drive's Secure Erase command, which is often a feature built into the drive's firmware.
2. Physical Destruction (The Absolute Guarantee)
For extremely sensitive data or non-functional devices, physical destruction is the most secure method, ensuring data can never be recovered. This method, however, renders the device unusable for recycling.
3. Cryptographic Erasure (Modern and Efficient)
This method is highly effective for devices that were already utilizing full-disk encryption (which is standard on many modern operating systems and devices). Instead of overwriting all the data, the user simply and securely destroys the encryption key that was used to scramble the data. Without the key, the encrypted data becomes mathematically unrecoverable.
A Step-by-Step Guide to Secure Device Disposal
Whether you're an individual or a business, follow these crucial steps to ensure a secure transition for your end-of-life device:
Phase 1: Preparation and Backup
Phase 2: Secure Data Wiping
Phase 3: Responsible Disposal

Compliance and Business Liability
For organizations, the stakes are significantly higher. Regulations like the GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), and various state-level data privacy laws mandate the secure handling and disposal of Personally Identifiable Information (PII) and protected health information (PHI).
Frequently Asked Questions (FAQ) About Data Wiping
Q: Does a quick format or full format secure my data?
A: No. A QUICK FORMAT does not secure your data because it only rapidly deletes the Master File Table or the equivalent file system index—much like tearing out the table of contents from a book—which simply marks the entire space on the drive as available for new files, leaving all the sensitive binary data intact and completely recoverable by any commonly available data recovery software until those sectors are physically overwritten.
While a FULL FORMAT offers a much higher degree of security than a quick format, especially on modern Windows systems where it typically overwrites the entire drive with zeros, which makes basic data recovery virtually impossible; however, for truly sensitive data, it is still not considered fully secure against advanced forensic recovery methods, which necessitates using a dedicated secure wiping utility that utilizes multi-pass erasure algorithms like the DoD 5220.22-M standard to ensure absolute data destruction.
Q: What is the NIST 800-88 guideline?
A: The NIST 800-88 Guideline, formally known as Special Publication 800-88, Guidelines for Media Sanitization (currently Revision 1 or 2), is a U.S. government document published by the National Institute of Standards and Technology that provides methodical and risk-based guidance for organizations to securely and permanently erase data from all types of electronic storage media, ensuring that the information becomes irretrievable to an unauthorized person or party, even with advanced forensic techniques. This essential standard — which superseded older methods like the DoD 5220.22-M — categorizes sanitization into three distinct levels: Clear (using logical overwriting to protect against simple recovery tools), Purge (employing physical or logical techniques like Cryptographic Erase or degaussing to protect against state-of-the-art laboratory recovery), and Destroy (physical destruction like shredding or incineration), allowing organizations to select the appropriate level of protection based on the confidentiality and sensitivity of the data, the type of media, and the planned future use or disposal of the storage device.
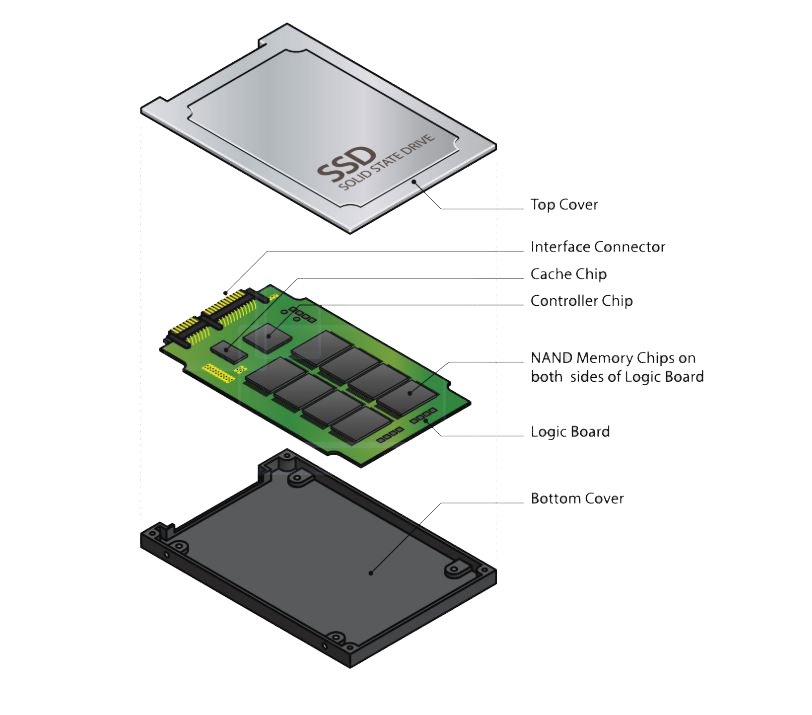
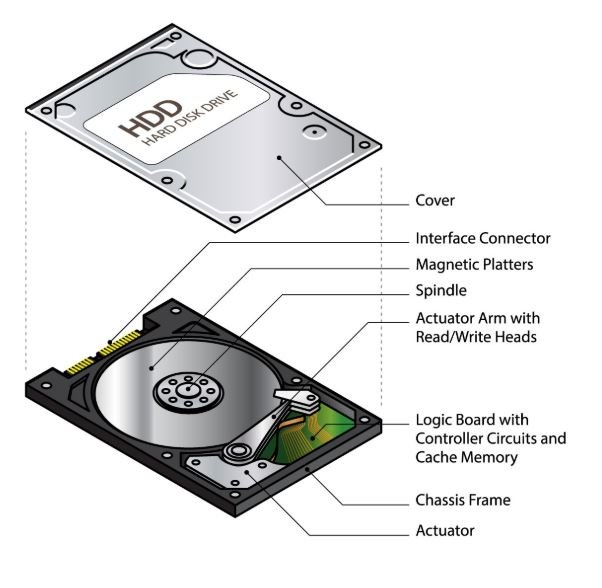
Q: Is my old magnetic HDD or newer SSD harder to wipe?
A: The newer Solid-State Drive (SSD) is technically harder to wipe securely using traditional software overwriting methods because of its internal architecture and complex controller logic, whereas a traditional magnetic Hard Disk Drive (HDD) is straightforwardly wiped by a single pass of data overwriting.
The difficulty with SSDs stems from how the controller manages the NAND flash memory.
HDD Wiping Simplicity
Conversely, the wiping of a magnetic HDD is much more predictable and simpler:
· Predictable Writing: HDDs write data directly to specific, user-addressable sectors on spinning magnetic platters, meaning a single-pass software overwrite (writing zeros or random data over the entire drive) is generally considered sufficient to prevent recovery, even by forensic laboratory techniques, according to modern standards like NIST 800-88.
· Degaussing Option: HDDs, due to their magnetic storage, also have the option of being degaussed (exposed to a powerful magnetic field), which completely randomizes the data, a method that is fast and totally effective for HDDs but has no effect whatsoever on non-magnetic SSDs.

In summary, while an HDD can be securely wiped with a simple overwrite or a powerful magnet, an SSD requires the use of specialized, low-level firmware commands to bypass its controller's internal data management logic and ensure all data, including that in addressable blocks, is erased.
Protecting your data at the end of a device's life is your final, most critical security measure. By moving beyond simple deletion and adopting industry-standard secure data wiping methods, you ensure that when your device is ready for its next life, your personal and corporate data is truly and permanently gone.
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0