
Small businesses are often targeted because they are perceived as having weaker defenses. You don't need a huge budget to be secure; you need a smart, layered approach.
1. Top Free and Low-Cost Cybersecurity Tools
Here is a curated list of essential, budget-friendly security layers:
Endpoint Protection (Antivirus/Anti-Malware)
· Core Purpose: Serve as the final security line by actively monitoring, detecting, and blocking malicious threats directly on individual user devices. This crucial defense ensures that devices like laptops and desktops are protected in real-time from viruses, ransomware, spyware, and other forms of malware, preventing these threats from compromising sensitive data or causing system disruption.
· Examples: CyberShield Ultimate Defense, Bitdefender, Malwarebytes, Advanced System Repair Pro
Password Management
· Core Purpose: Significantly enhance an organization's security posture by enforcing strong, unique passwords for every account while simplifying the login process for employees. This is achieved by storing all credentials in an encrypted, centralized vault, automatically generating complex passwords, and facilitating secure sharing, ultimately protecting the business from the widespread threat of weak, reused, or compromised login information.
· Examples: Bitwarden, LastPass.
Multi-Factor Authentication (MFA)
· Core Purpose: Create a layered defense that prevents unauthorized access by making a stolen or guessed password insufficient to breach an account. It does this by requiring a user to successfully present verification from at least two different categories—something they know (like a password), something they have (like a phone or security key), and/or something they are (like a fingerprint). The ultimate goal is to significantly reduce the risk of account takeovers, phishing, and data breaches, with studies showing it can stop over 99% of automated attacks.
· Examples: Google Authenticator, Microsoft Entra ID (included with Microsoft 365).
Email Security
· Core Purpose: Protect the most common and exploited communication channel—email—from cyber threats that seek to steal data, deploy malware, or commit financial fraud.
Email is the primary pathway for over 90% of successful cyberattacks because it relies on human trust and is used by virtually every employee. Therefore, email security acts as a vital layer of defense to ensure the Confidentiality, Integrity, and Availability of both communications and the entire network.
1. Stop Malicious Content: To automatically detect and block emails containing phishing links, ransomware, viruses, and other malware before they reach a user's inbox.
2. Prevent Unauthorized Access (Spoofing & Takeover): To authenticate the sender and prevent attackers from impersonating trusted individuals (like a CEO or vendor) to trick employees into sending money (Business Email Compromise or BEC) or giving away credentials.
3. Protect Sensitive Data: To ensure that private, confidential, and regulated information (like financial details or customer PII) remains protected through measures like encryption and Data Loss Prevention (DLP), both while in transit and at rest.
· Examples: Microsoft Defender for Office 365, Proofpoint Essentials, MimeCast, Barracuda Email Protection, IRONSCALES
Network Security (Firewall/DNS)
· Core Purpose: Establish and enforce policies that safeguard all digital assets by ensuring the Confidentiality, Integrity, and Availability (CIA) of the network and its data. This defense prevents unauthorized access, misuse, modification, or denial of a computer network and its resources. The Firewall serves as the network's primary barrier, inspecting and filtering all incoming and outgoing traffic to block external threats and enforce internal access rules. Meanwhile, DNS security is crucial for preventing connections to known malicious domains, thereby neutralizing threats like phishing and malware before they can even enter the network. Together, these layers of security are essential for mitigating cyber risks, maintaining business continuity, and complying with data protection regulations.
· Examples: pfSense, Cisco Umbrella, CyberShield Ultimate Defense, Advanced System Repair Pro
Backup & Recovery
· Core Purpose: Ensure business continuity by safeguarding all critical data and systems against loss or corruption. Specifically, it involves creating secure copies of data (Backup) to an off-site or safe location, protecting it from hardware failure, human error, natural disaster, or cyberattack. The Recovery process then guarantees that this preserved data can be rapidly restored to its original or a new location, minimizing downtime and achieving target recovery objectives. This process is absolutely essential for upholding the Availability and Integrity components of an organization's overall data security strategy.
· Examples: Acronis True Image, Backblaze Business.

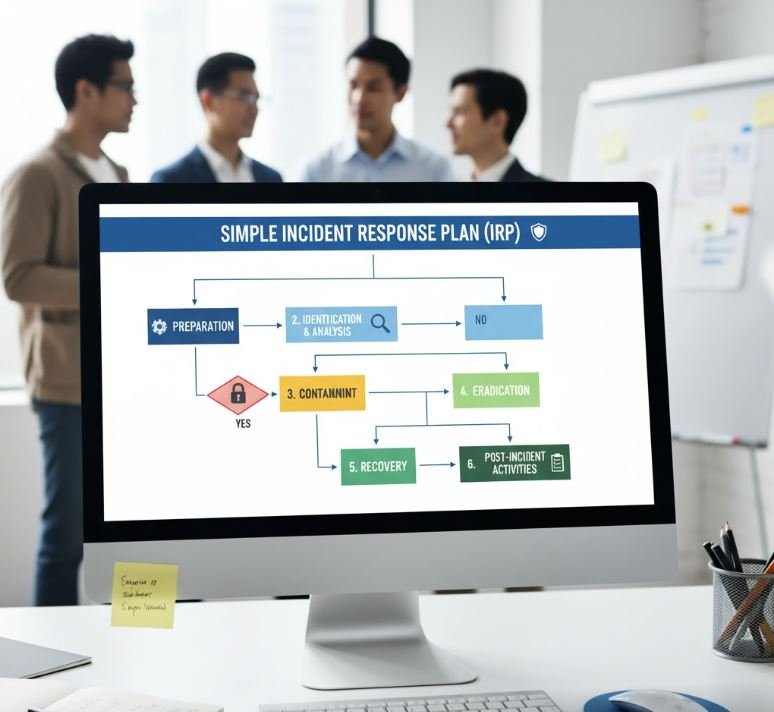
2. Simple Incident Response Plan (IRP) Template
A simple Incident Response Plan (IRP) ensures your team knows exactly what to do when a cyber event occurs, minimizing panic and damage.
The Six Core Phases of Incident Response
This foundational phase involves establishing the necessary people, processes, and technology before an incident occurs. Key activities include forming an Incident Response Team (IRT), defining roles, documenting procedures, creating communication plans, and acquiring the necessary forensic and security tools. Security Management and Executive Leadership establish the IR plan, define roles, acquire tools, and conduct training before any incident occurs.
This is the process of detecting a security event (like an alert from a monitoring system) and determining whether it is a true incident. The IRT analyzes all available data (logs, network traffic, alerts) to confirm a breach, determine its scope, classify its severity, and document the initial evidence. The SOC Analyst detects an alert, investigates the potential event, confirms a security incident, and escalates it to the Incident Response Team (IRT).
Once an incident is confirmed, the immediate goal is to limit its scope and prevent further damage. Containment strategies involve short-term actions (e.g., isolating compromised systems or accounts) and long-term planning to preserve evidence while halting the threat's spread. The Incident Handler and System Administrators take immediate action to isolate the affected systems to stop the attack's spread and minimize ongoing damage.
After the threat is contained, the team must eliminate the root cause of the incident. This involves removing all traces of the attack—such as deleting malware, patching the vulnerability that was exploited, and remediating all compromised systems to ensure the attacker is fully expelled. Forensics Specialists perform a root cause analysis, and Security Engineers remove all traces of the malware, unauthorized access, and exploited vulnerabilities.
In this phase, the affected systems are restored to a clean, production-ready state. This typically involves restoring data from verified, clean backups, rigorous testing to confirm system integrity, and monitoring the systems closely before fully returning them to normal operation. IT Operations and System Administrators restore clean backups, rebuild affected systems, and monitor them rigorously before returning them to production service.
This final, but critical, phase involves a post-incident review to analyze what happened, how the team responded, and what improvements are needed. The findings are used to update the security policy, revise the Incident Response Plan, improve detection capabilities, and provide further training to staff, completing the continuous improvement cycle. The Incident Commander leads a review to document what happened, identify deficiencies in the response, and update policies for future preparedness.
Pro-Tip: Keep a printed copy of your IRT contacts and the containment steps off-site or on a non-networked device (like a personal phone), in case network access is lost.
3. Cost-Effective Security Monitoring Checklist
Security monitoring is the process of watching your systems for signs of an attack.
In today's threat landscape, security is not a luxury—it's a necessity. However, robust protection doesn't always require an enterprise-level budget. The most cost-effective strategy involves prioritizing high-impact, low-cost actions and maximizing the effectiveness of the tools you already own.
The most powerful and affordable security layer you have is your staff. Focusing on human controls minimizes the risk of social engineering and accidental breaches, which account for a majority of successful attacks.
These practices leverage human intelligence and process discipline for maximum defense at zero monetary cost.
This category emphasizes that the strongest and cheapest layer of security is an informed, disciplined workforce and clearly defined procedures. By investing in processes rather than products, organizations tackle the root cause of most breaches: human error and misused credentials.
Before subscribing to expensive security platforms, leverage the powerful monitoring tools that are already integrated into your operating systems and network hardware.
This approach focuses on getting maximum utility and visibility from the security components that are either built into operating systems or available as highly functional community/open-source projects, avoiding expensive licensing fees.
3. Resilience Monitoring: Testing Your Safety Net
If an attacker successfully breaches your defenses, the cost of recovery is directly tied to the quality and availability of your backups. This is the ultimate cost-saver against crippling financial loss from ransomware.
Resilience monitoring shifts the focus from preventing the breach to surviving it. The most significant financial saver against ransomware and catastrophic failure is a confirmed, working backup and a tested recovery plan. This phase is about ensuring your financial safety net is secure and operational.

 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0