
Removable Media Threats: The Hidden Danger of Infected USB Drives and External Storage
The humble USB flash drive and other external storage devices offer unparalleled convenience for data transfer, but this portability comes with a significant and often underestimated security risk. Removable media devices are a preferred method for cybercriminals to bypass traditional network defenses, turning a simple storage tool into a potent vector for malware and data theft.
The Mechanisms of Attack: More Than Just a Virus
The threat from removable media extends far beyond simple file-based viruses. Attackers employ sophisticated methods to compromise devices

Impact on Individuals and Organizations
The consequences of inserting an infected external device can be severe for both home users and large enterprises:
Best Practices for Defense
Mitigating the threat from removable media requires a combination of technology and vigilance.
Recommended Action: Never Plug in Unknown Devices
Why It’s Effective: This is the single most important rule. If you find a drive, do not plug it into any computer. Hand it to IT or security personnel.
Recommended Action: Disable the 'Autorun' Feature
Why It’s Effective: The Autorun or AutoPlay feature on Windows and other OSs automatically launches programs or displays content when a device is inserted. Disabling this prevents many file-based threats from running automatically.
Recommended Action: Scan All Removable Media
Why It’s Effective: Before accessing any files, always use up-to-date antivirus/anti-malware software to scan the entire drive. Many modern security suites offer a prompt to scan upon insertion.
Recommended Action: Encrypt Sensitive Data
Why It’s Effective: Use strong encryption on your own external drives so that if they are lost or stolen, the data remains protected.
Recommended Action: Use Endpoint Security Solutions
Why It’s Effective: For organizations, using solutions that provide Device Control can restrict or log the use of external devices, preventing unauthorized connections and data exfiltration.
Recommended Action: Security Awareness Training
Why It’s Effective: Educate yourself and employees about the risks of social engineering tactics like the "USB drop," as the human element remains the weakest link.
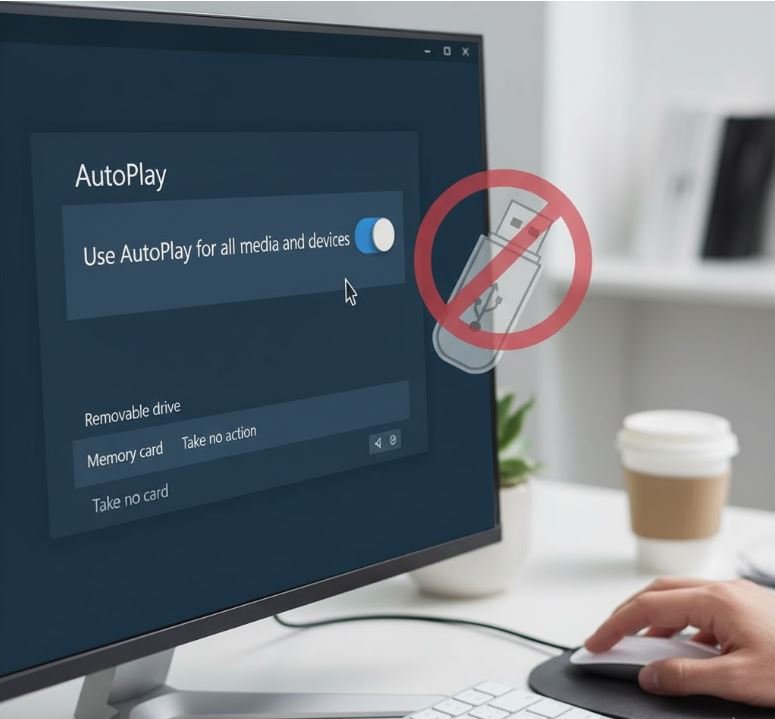
Disabling the AutoPlay feature prevents Windows from automatically executing programs or opening files when a removable device (like a USB drive or SD card) is inserted.
1. Click the Start Menu and select Settings (the gear icon).
2. Select Bluetooth & devices (or Devices on older versions of Windows 10).
3. Click on AutoPlay in the left-hand menu.
4. Toggle the main setting "Use AutoPlay for all media and devices" to Off.
5. Under the sections "Removable drive" and "Memory card," select "Take no action" from the drop-down menus.
This method is not available on Windows Home editions.
1. Press the Windows Key + R to open the Run dialog.
2. Type gpedit.msc and press Enter to open the Local Group Policy Editor.
3. Navigate to: Computer Configuration $\rightarrow$ Administrative Templates $\rightarrow$ Windows Components $\rightarrow$ AutoPlay Policies.
4. In the right-hand pane, double-click on "Turn off AutoPlay."
5. Select Enabled.
6. In the "Turn off AutoPlay on" drop-down menu, select "All drives."
7. Click Apply and then OK. You may need to restart your computer for the change to take full effect.
For a business or organization, relying on individual users to manage Autorun isn't enough. Endpoint Security Solutions (specifically those with a Device Control module) provide a centralized, granular way to manage all removable media.
Feature: Granular Control
Description: Allows administrators to set rules based on the user, computer, or even the specific brand/model of the USB drive.
Benefit: Blocks all unauthorized devices while permitting approved ones for essential tasks.
Feature: Whitelisting
Description: Only explicitly approved USB devices (identified by their unique Hardware ID) are allowed to connect.
Benefit: Blocks all unauthorized devices while permitting approved ones for essential tasks.
Feature: Data Encryption Enforcement
Description: Mandates that any data copied from the corporate network to an approved USB drive must be automatically encrypted.
Benefit: Protects sensitive data in case the authorized drive is lost or stolen.
Feature: Monitoring and Auditing
Description: Logs every single connection, file transfer attempt (blocked or allowed), and device use.
Benefit: Provides a clear audit trail for compliance and helps investigate security incidents.
Feature: Bad USB/HID Protection
Description: Some advanced solutions can detect and block devices that try to impersonate a keyboard or other input device.
Benefit: Defends against sophisticated, hardware-based attacks like the Rubber Ducky.

By treating every external storage device with a healthy degree of suspicion, users can significantly reduce their risk exposure and protect their systems from these ever-present, portable threats.
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0